What is an MX record?
The Domain Name Server (DNS) is a core part of the working internet, allowing for the mapping of domain names to IP addresses. A DNS has an entry known as an MX (mail exchange) record. The MX acts like a postal service to ensure an email is delivered to its correct recipient. In other words, the MX record specifies the correct email server for a given domain, directing emails to the intended recipient using a standard protocol, such as Simple Mail Transfer Protocol (SMTP). The process is neat and straight forward, and the smooth digital communications using email depend on it.
MX records are publicly available. This makes them a potential source of intelligence for a cybercriminal. Attackers, for example, can use the MX record to create targeted phishing campaigns. Additionally, cybercriminals develop attack techniques that leverage the capabilities of the MX record. A technique called a DNS MX record hijacking attack is used to intercept emails. In one attack, compromised login credentials were used to access admin accounts and change the DNS records of cryptocurrency platforms. Once modified, the attackers could then hijack public websites and private email servers.
MX records have, however, been developed to integrate some intrinsic security features.
How does an MX record provide email security?
An MX record isn’t just used to deliver an email to the correct destination. An MX record is also used to provide basic email security. Email authentication protocols used by DNS MX include SPF, DKIM, and DMARC.
DMARC (Domain-based Message Authentication Reporting& Conformance) is a record published in the DNS. This record uses DKIM (DomainKeysIdentified Mail) and SPF (Sender Policy Framework) protocols to prevent domain spoofing. DMARC is part of an email domain policy. The policy is shared and authenticated using DKIM and SPF protocols. If the email authentication process under DKIM and SPF fails, DMARC can mark the emails as spam or prevent the emails from being delivered.
DMARC, DKIM, and SPF are essential protocols that enhance fundamental email security. However, email-borne attacks are highly sophisticated and require additional layers of protection.


MX records and AI-powered email threat prevention
Email threats are evolving. Cybercriminals are using increasingly sophisticated techniques that allow malicious emails to go under the radar of integral security measures, such as DMARC. Evasive tactics include using QR codes to obfuscate malicious links and polymorphic malware that continually changes to hide from conventional detection. As such, email security requires a more proactive approach to protecting a company from email-borne threats.
Features of advanced email threat detection and prevention
While DMARC is an essential built-in email security feature, email security solutions must utilize a collection of unified technologies to identify and prevent malicious emails. MX record-driven, secure email solutions seamlessly integrate with an organization's MX records, ensuring a secure and reliable email experience. The security solution works alongside the intrinsic security and efficiency of MX records to add layers of proactive security measures that protect a company, including against MX-targeted threats. This next-generation email security is known as Integrated Cloud Email Security (ICES). Any organization exploring ICES solutions should consider the following features:
Speed
Advanced email security solutions must not delay delivery. The ability to differentiate between legitimate and spam emails quickly and accurately is a fundamental feature of an email filter.
Accuracy
The email filter must have a high catch rate (close to 100%) for spam, phishing and malware.
Cloud-native
Modern email threat prevention must be cloud-based to allow rapid deployment and easier management.
Integration with Microsoft 365
API integration with M365 reduces any impact on normal working conditions. ICES solutions should scan all emails (internal and external) to augment EOP and MS Defender, delivering exceptional phishing protection.
Real-Time Blacklists and SURBL filters
These are used to cross-check the sender's email and IP addresses against global blacklists of known spammers.
Bayesian analysis
This mathematical model is used to calculate the likely probability of an email being spam or malicious.
AI-powered Antivirus
Emerging threats are not prevented by DMARC. An antivirus engine must be able to scan and analyze email attachments, detect embedded hyperlinks in emails, and identify those that exploit zero-day vulnerabilities and new and emerging threats.
AI-powered phishing detection
Phishing campaigns now use AI to generate personalized phishing attacks that are difficult to detect. AI-powered anti-phishing utilizes techniques such as Natural Language Processing (NLP) to detect unusual language patterns that indicate phishing.
Sandboxing
Protects against sophisticated spear-phishing and malware. Suspicious emails are placed in a sandbox, allowing administrators or managed service providers/security professionals to check the email in a safe environment.
Time-of-click protection
URL rewriting is a technique used to prevent users from navigating to spoof websites. The rewrite is performed in real time.
Audit and history
Comprehensive audits and history must be available from a central console.
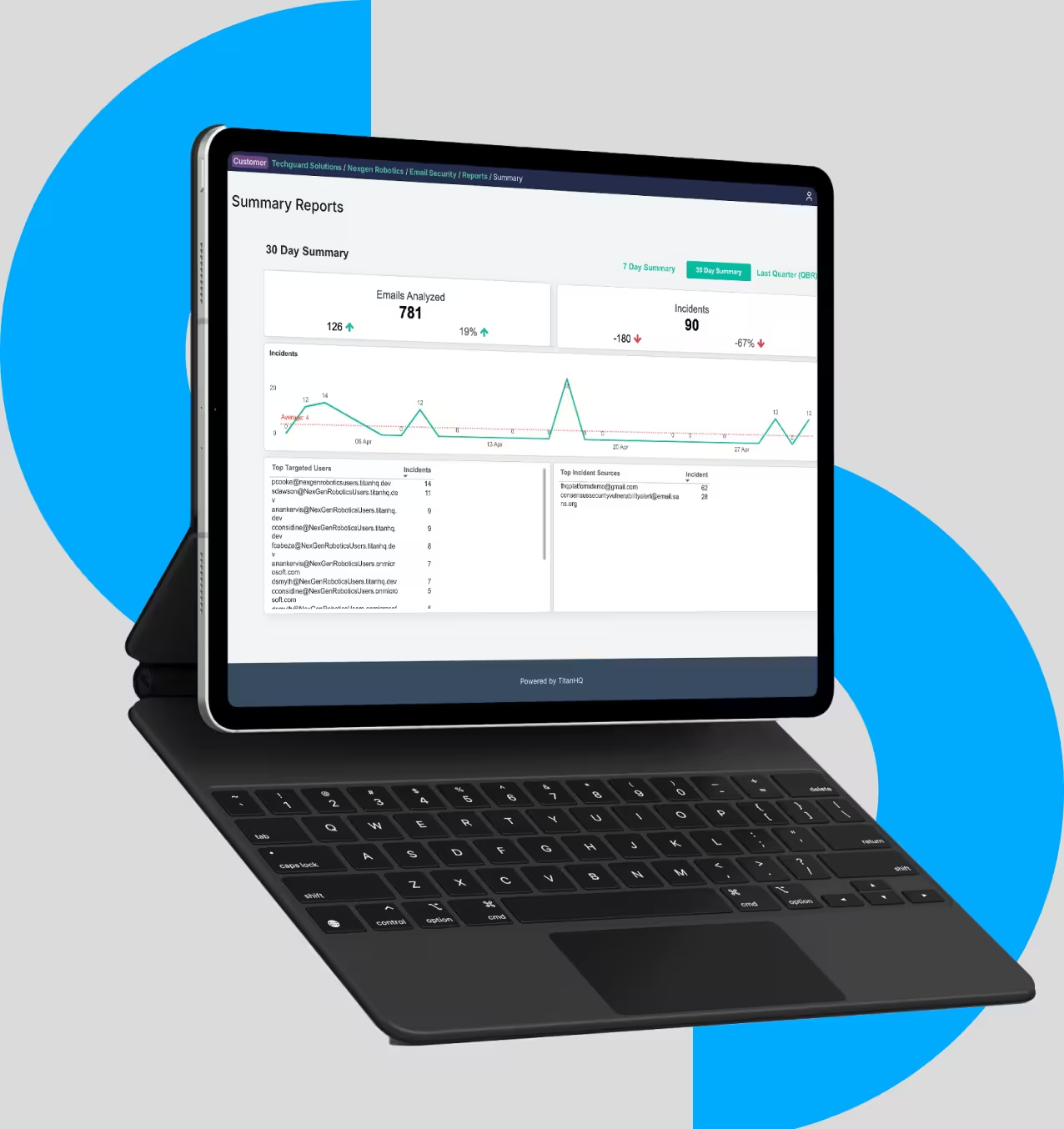
MSP delivered email threat prevention
Managed service providers (MSPs) can strengthen client security by combining MX record protection with advanced Integrated Cloud Email Security (ICES) solutions. To deliver effective, scalable protection, MSP offerings should go beyond the core features of ICES and include three key pillars:
Multi-tenant management
A centralized, cloud-based console that lets MSPs manage all customers in one place, reducing administrative overhead.
Automated protection
Fast, automated onboarding to quickly add new accounts without manual complexity.
Cross-sell readiness
Seamless bundling with Microsoft 365, Azure Blob, and Entra ID to increase value and margins.
While MX records ensure emails are routed to the right destination, they cannot by themselves defend against today’s AI-driven, evasive email threats. That’s why advanced, AI-powered email security is an essential layer for MSPs to deliver robust protection against evolving cyberattacks.
Ready to get started?